Supreme Info About How To Develop Firewall
One key player in this digital safety game is the firewall, your network's trusty guardian against cyber baddies.
How to develop firewall. Without it, the question is no longer if but when malicious attacks will harm you, unfortunately, are common on the internet. Googling any of these will point. Firewalls create a layer of protection against unauthorized access to your network.
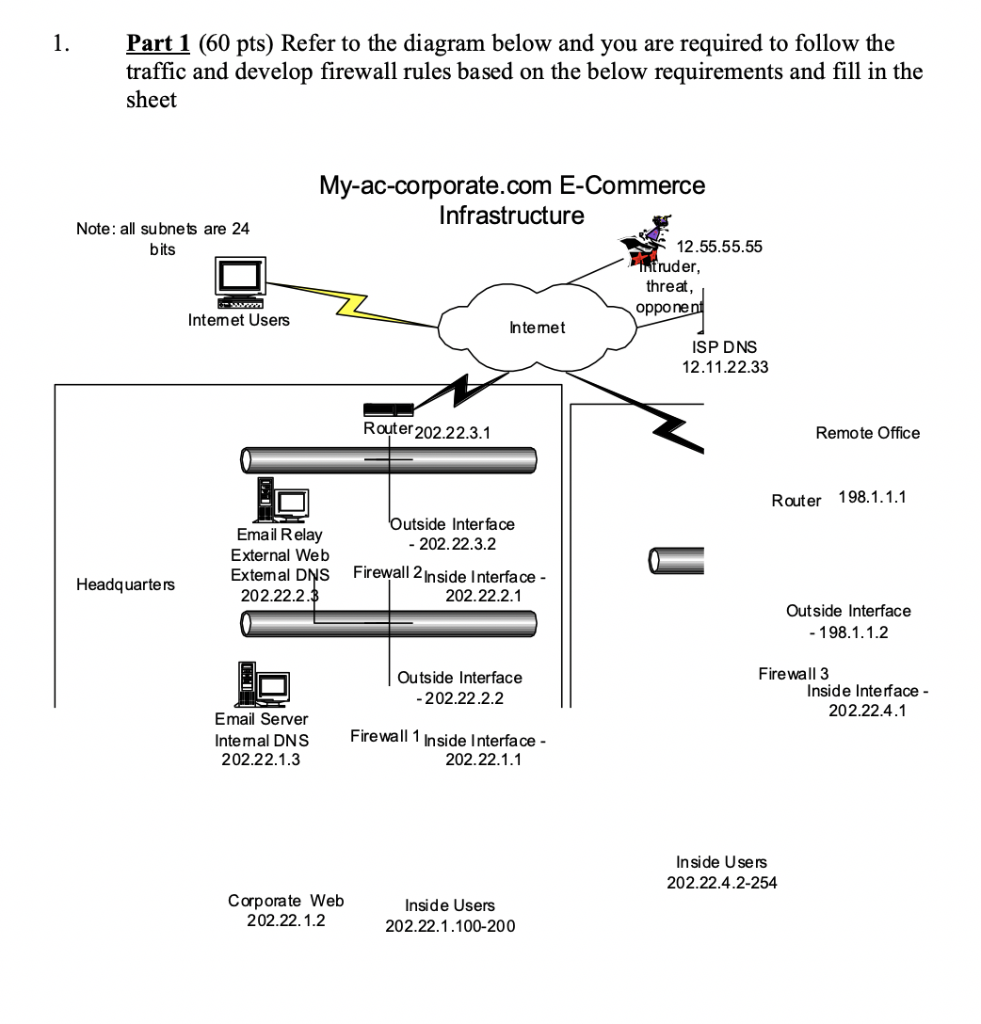
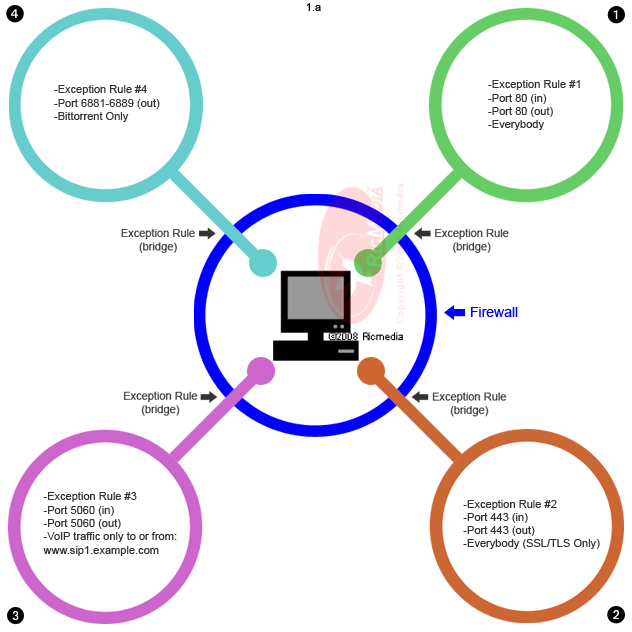
Feeling a bit swamped by the world of network security? In general, the purpose of a firewall is to reduce or eliminate the occurrence of unwanted network communications while allowing all legitimate communication to flow freely. But for traffic to move from a lower to a higher level, a different set of filtering rules are deployed.
A firewall is a system that is designed to prevent unauthorizedaccess from entering a priva. Each region in the firewall system is allocated a security level. This will involve checking the security requirements as.
Let's start with the essentials in our firewall 101 guide. Enter the name you want to give your firewall, and the domain associated with your internal office network. This is an animated video explaining what a network firewall is.
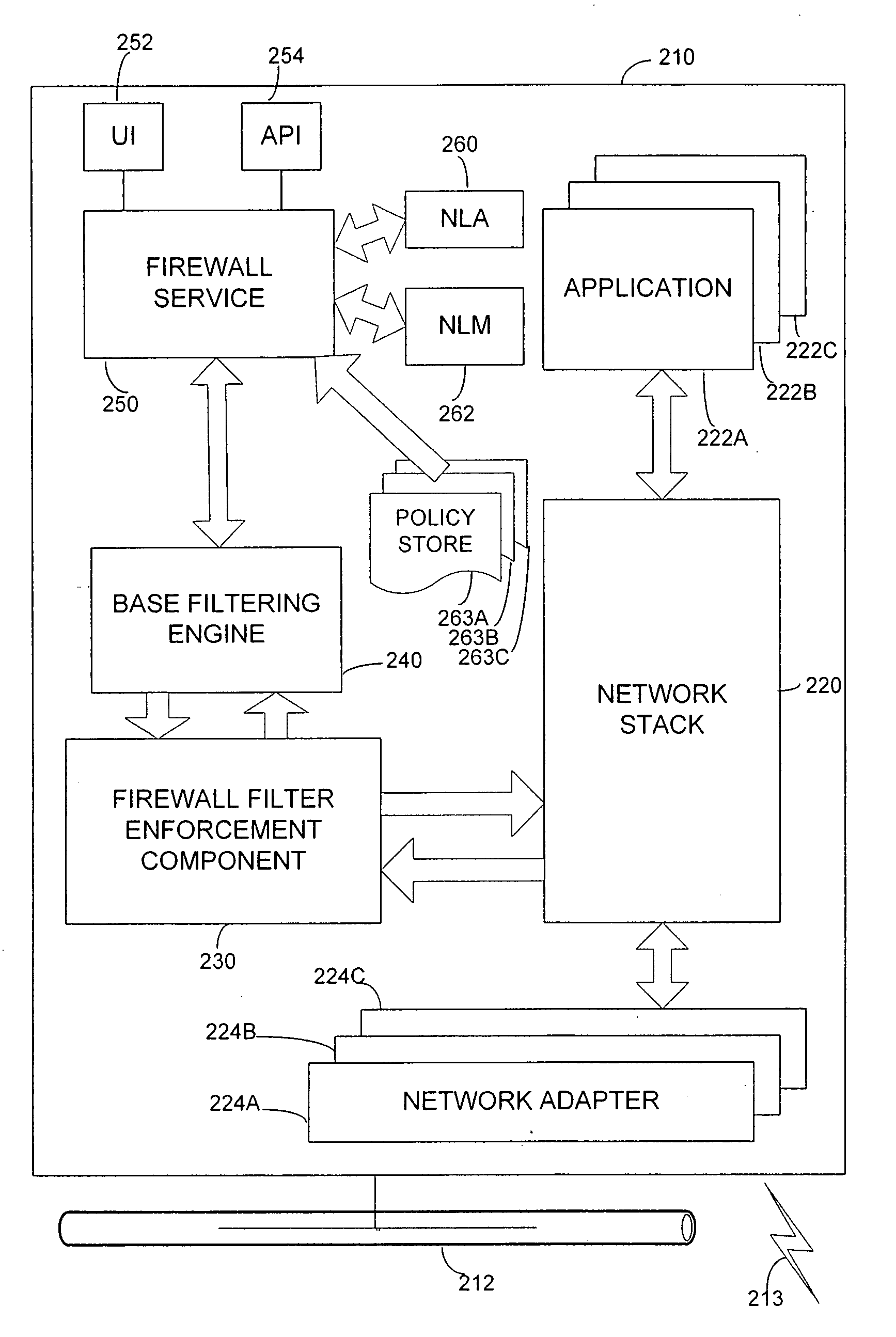
Linux uses netfilter and iptables. For example, low, medium, and high. But for any real application, it's much safer and smarter to build a shell around the existing firewall api.
You will be presented with the initial setup wizard. You can also block and/or bandwidth shape sends. Free firewall applications for linux are numerous.
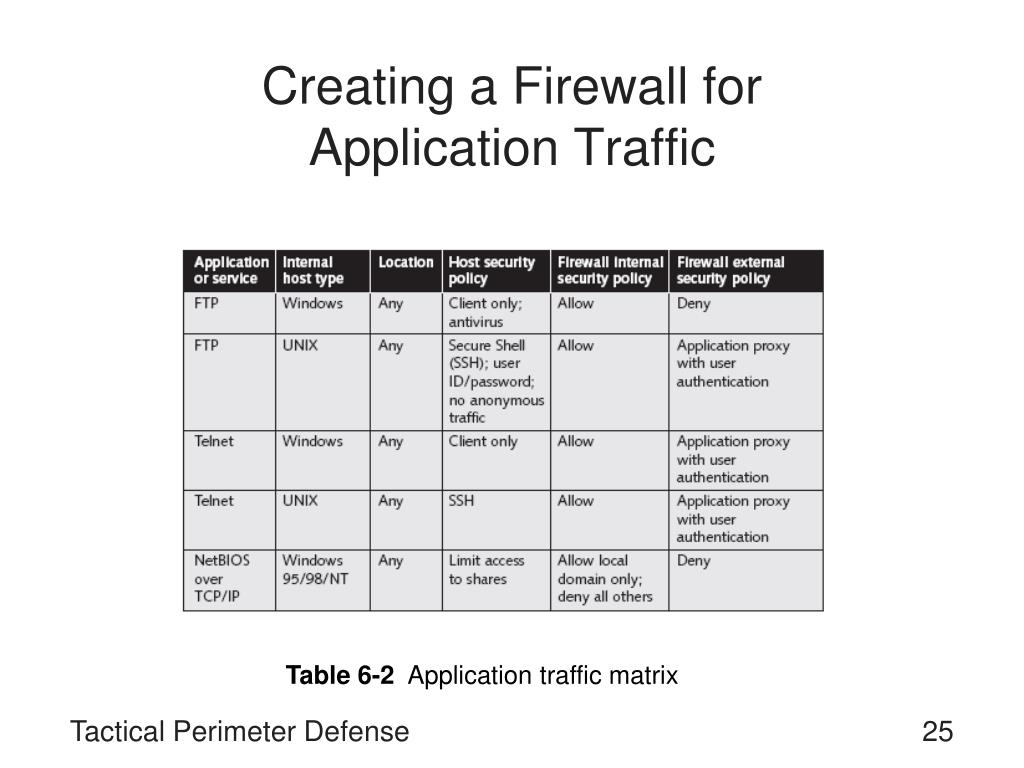
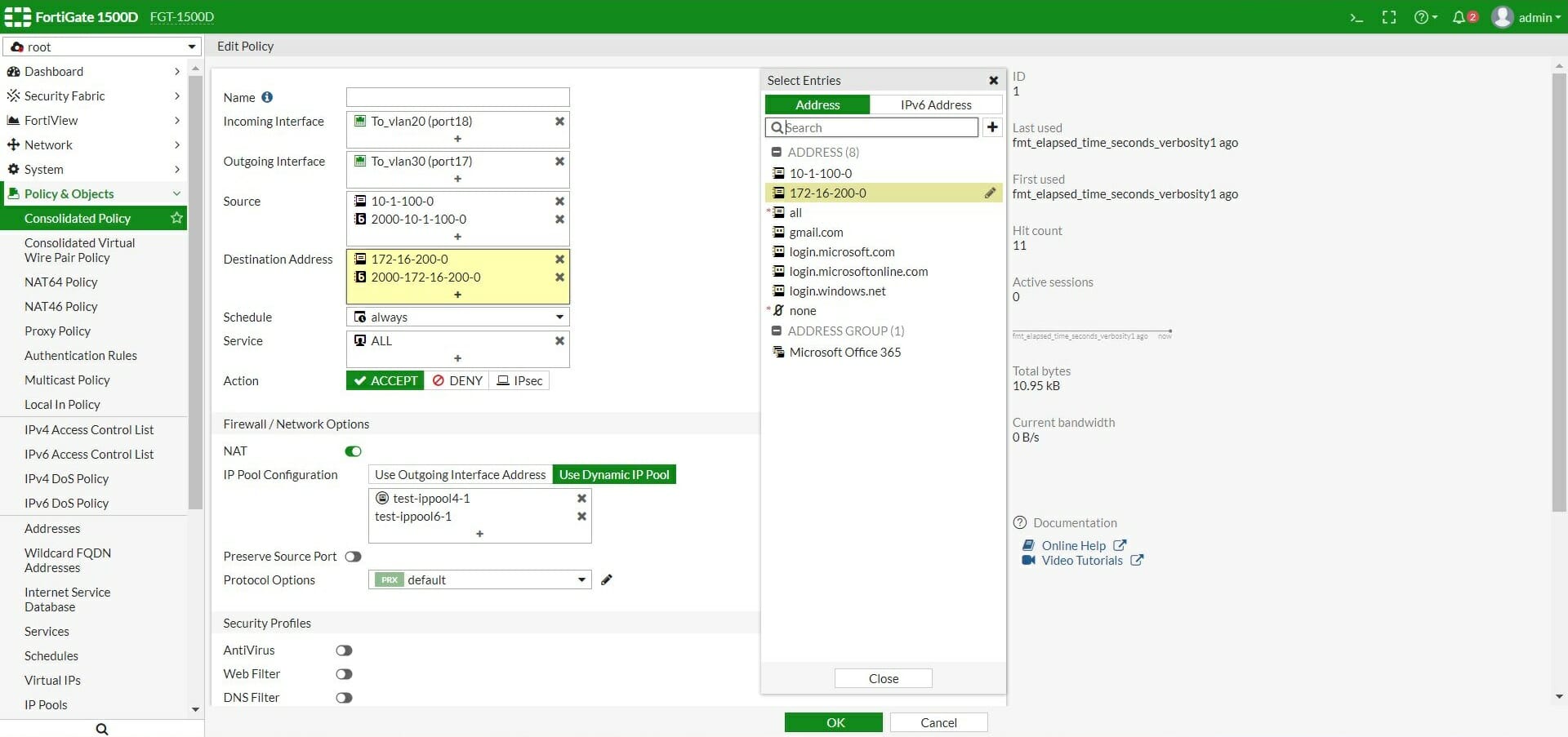
Pinpoint the kinds of security controls your organization needs. Zones and interfaces allow and deny by service name allow and deny by port number firewalld rich rules conclusion nowadays, configuring and implementing a reliable firewall for your servers and network is a must. Secure your firewall (seems redundant, we know.) administrative access to your firewall should be limited to only those you trust.
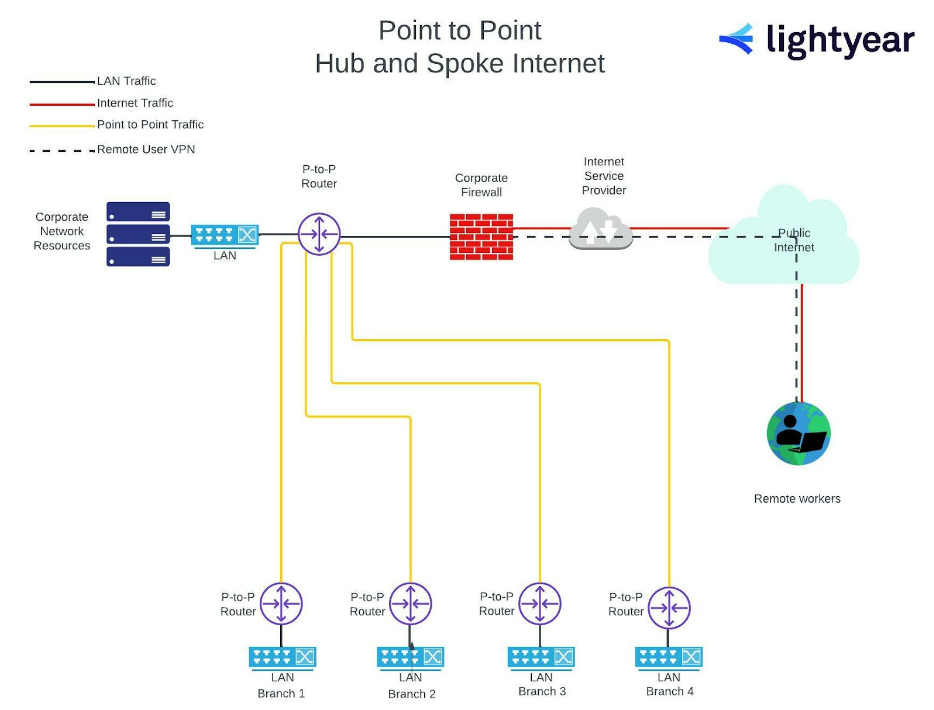
What i can do is set up a firewall in front of a web server that's protecting just the web server itself because there are so many unique attacks that they only go for that particular type of. Click on next, then next again at the following screen to begin the setup of your new firewall. Firewalls prevent viruses and malware from infecting systems and spreading throughout the network.
Configure firewall logging to capture comprehensive data on network traffic and connection attempts. Firewalls are essential to protecting assets across your digital landscape from potential cybersecurity threats. You can block receives, but you can't really shape receives at tdi, because you're not allowed to pause (the receive code path executes at.
You can do firewall stuff at the tdi level and it's nice there, since you can associate sockets with applications (which you can't do at ndis). The following firewall design principles can ensure you have the most secure defense system: Developing a firewall implementation framework that addresses your most pressing security needs will enhance your overall cybersecurity.